We recently had a compromise on one of our hosted websites. In this article we wanted to talk about how we caught & contained the compromise before it could cause any damage. Read on if you’re interested in our approach to WordPress hosting security.
It’s super interesting stuff, if you’re a little geeky, and we think helps illustrate why having a committed technology partner in your corner is key! Let’s start at the beginning…
The Compromised Website
For privacy, we’re not going to disclose the website that was compromised. Basically, It was a B2B website running the e-commerce system WooCommerce, along with some extra plugins and a theme with our page builder.
The attack started innocently enough, with a user registration on the website. Our team quickly caught this registration because:
- The email address used looked suspicious.
- The user triggered an out-of-the-ordinary WordPress registration email.
Upon seeing the registration our team jumped into action.
Proactive WordPress Security
First our team logged into the website & identified the user account. At this point we discovered that the account was an Administrator, we quickly removed these permissions from the user. We kept the account for further analysis and to buy some time.
Next we figured out how the account was registered. We scanned for vulnerabilities and found a recently disclosed critical exploit in TI WooCommerce Wishlist. The exploit allowed an attacker to register a new user account & make it an administrator.
The way this exploit worked, leaned in our favor. Remember that we didn’t delete the account earlier, this helped us, the exploit to get admin rights only worked for new user accounts. The hacker was left fumbling around once he discovered his new account didn’t have the permissions he needed, by the time he realized, it was already too late.
We resolved this breach by restoring a backup, just in case the hacker had installed any malicious code. Then we applied the patch for the exploit and began restoring any data lost.
Post-Mortem
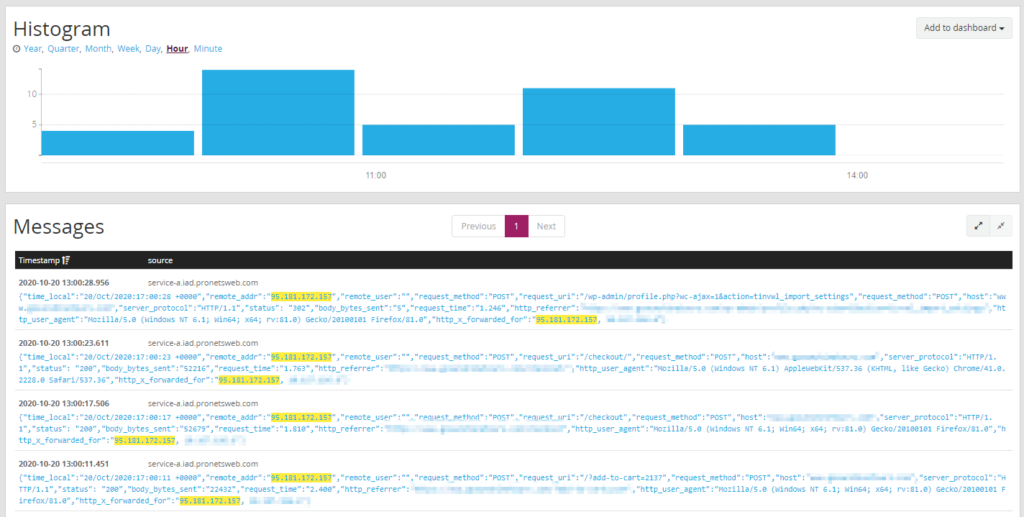
Once the breach was contained, we could look at what happened & whether any data was compromised.
The site itself was safe, since we restored backups. As well, we had no concerns about other sites on the server, since all of our websites are fully isolated from each other.
We checked out our logs to see what the hacker did. We identified the point that he breached the site and what he did from that point. Due to our fast response he was not able to export any data, install any malicious code, or access the administrative backend.
We quickly took steps to patch our other sites and monitored this hacker for a while longer. He sniffed out one of our other sites but was unable to use the exploit since we patched it.
Key Takeaways:
- All software has security issues – frequent patching and monitoring are key.
- An unmonitored site is dangerous – it is key to have a hosting team that looks out for you.
- Not all compromises can be prevented – a proactive response keeps you & your sensitive data safe.
Get Secure WordPress Hosting
With us, your website isn’t just a number. Host with us and get top-notch security, performance, and support from our personal team.